Camera apps might be making you look better while stealing your data and infecting you with malware
Reportedly, team CyberNews has caught numerous Android camera apps spying on users. These apps also include some popular beauty-filter applications with a large number of downloads as well.
As elaborated in their blog post, these apps that apparently provide fun to the users, secretly scrape their data. Consequently, the developers behind these apps use this data for monetization.
In brief, around 30 of the most popular camera apps with millions of downloads, seemingly belonging to the same or similar developers, involved in spying activities.
As discovered, these apps seek dangerous permissions to access unnecessary details. These include access to contacts, GPS location, coarse location, and access to read and write files on the device, apart from the anticipated permissions to access camera and microphone.
But in the background, you’re not expecting these apps to scrape and sell your data, plague you with nonstop, malicious ads, redirect you to phishing websites, or even spy on you.
But that’s exactly what some of the top beauty camera apps have been found guilty of doing. Some of the noteworthy apps making to this suspicious app list include
BeautyPlus – Easy Photo Editor & Selfie Camera
Selfie Camera – Beauty Camera & Photo Editor
HD Camera Selfie Beauty Camera
B612 – Beauty & Filter Camera
BeautyPlus – Easy Photo Editor & Selfie Camera, with 300 million installs, which was identified as being either malware or spyware. Its developer, Meitu, was suspected of collecting user data in its Chinese servers, and then selling it. There’s also the app developer iJoysoft, whose apps are connected to malicious adware. Lyrebird Studio, the developer behind Beauty Makeup, Selfie Camera Effects, Photo Editor, was identified by Trend Micro for sending users pornographic content, redirecting them to phishing sites, and collecting their pictures.
How The Apps Abuse Exfiltrated Data The main purpose of all the data exfiltration through these apps is for monetary gain. The more data these developers gather from the users, the more money they will make.
Results
- More than half (16) of these apps are based in Hong Kong or China
- One app doesn’t ask for permission to use your camera, but turns the camera on anyways without any permission
- Three seemingly separate developers seem to be run by the same group, and may be connected to apps previously found to contain a widely-dispersed Trojan
- The top-ranked app developer Meitu, with more than 300 million installs, had apps identified as malware, violating Google’s ad policies, or secretly collecting data
- One app developer was found to install malware through its software
- One app was accused of sending users pornographic content, redirecting them to phishing sites, or collecting their pictures
- These apps are requesting up to 7 dangerous permissions, 5 on average, most of which are unnecessary for the app to function
- Unnecessary permissions include recording audio, using GPS, and seeing users’ phone statuses
- While only a few permissions are required for the app function, one app includes a whopping 40 total permissions
Three app developers seemed to be from the same group based in China. Even worse, they’re potentially connected to malware previously discovered.
The app developers Coocent, KX Camera Team and Dreams Room are seemingly separate developers with similar app offerings:
These app offerings are pretty similar: camera apps, music or audio apps, flashlight apps, and weather apps. The icons are also quite similar.
However, when we looked at the privacy policies for these three developers, we found that they’re all hosted on the exact same domain:
The domain hosting these three apps’ privacy policies, aliyuncs.com, is from Alibaba Cloud Computing (Beijing) Co., Ltd.
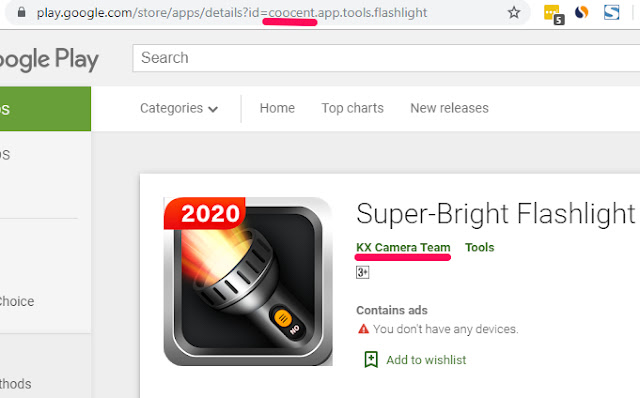
We can even see the Coocent’s privacy policy extension is named KuXun (a sound similar to Coocent), and which is reflected in KX Camera Team’s name. KX Camera Team has another app, Super-Bright Flashlight, which even has “coocent” as part of its app ID (which is unchangeable after it’s been created):
Then there’s Coocent’s non-active Twitter account, which has some important information you can see right from the search results page:
Those Chinese characters at the end – 中华人民共和国 – translate to the “People’s Republic of China”, the formal name for China.
Because of all that, the app developers Coocent, KX Camera Team and Dreams Room are all from the same group and they are based somewhere in China.
Another app developer, Istanbul-based Lyrebird Studio, creator of the camera app Beauty Makeup, Selfie Camera Effects, Photo Editor,was identified in research by Trend Micro to be one of many apps that send users porn, redirect them to malicious phishing sites, or collect their pictures.
Too many dangerous permissions:
Most obviously, camera apps will require about two dangerous permissions in order to function: CAMERA (to take pictures) and WRITE_STORAGE (to save your edited images).
These apps are requesting an average of 5 dangerous permissions, with one app requesting 7 dangerous permissions.
So what dangerous permissions are they requesting?
- 1 app wants the ability to scan your contacts list
- 13 apps want access to your GPS location
- 10 apps want access to your coarse location (via cell towers and wifi networks)
- 23 apps want access to your microphone
- 30 apps want the ability to write files to your device
- 29 apps want access to your camera
- 29 apps want the ability to read files on your device
It becomes important then to ask why a beauty camera app needs to record audio, track your GPS location, or go through your contacts list.
What these apps want with all your data
When looking at the past problems these app developers have had with data collection, the answer may become very obvious: money.
App developers can make lots of money by selling all your data to advertisers. Location-sharing agreements between app developers and app brokers – where apps can send your GPS coordinates up to 14,000 times per day – can bring in a lot of revenue. With just 1,000 users, app developers can get $4/month. If they have 1 million active users, they can get $4,000/month.
And that’s from just one broker. If they work with two app brokers with similar payouts, and have at least 10 million active monthly users, they could stand to make $80,000/month. With more dangerous permissions given by the user, they will get more sensitive data, which means they’ll make more money.
And that’s why these apps are free.
The cheaper apps, of course, take the easier route and simply flood their apps with non-stop, full screen ads that will cause their users to delete the apps sooner or later.
Essentially, you have to consider these important points:
- These apps are non-essential, as they provide no crucial function
- The top-ranked apps are created by developers with spotty reputations, outright malicious behavior, or using unethical practices
- There are bigger, more dependable apps out there that have similar features, are more accountable and with a clearer ownership structure, such as Messenger, Snapchat, Instagram, etc.
These are non-essential apps that seem to be quite risky. Therefore, we recommend that you practice caution on deciding whether or not to download these apps at all.








Comments
Post a Comment